In today’s world, cybersecurity is a top priority. As businesses continue to adopt digital technologies, they become more vulnerable to cyberattacks and data breaches. A well-structured Cybersecurity Checklist is a powerful tool to help organizations protect their valuable digital assets. It provides a clear framework to ensure that every aspect of cybersecurity is covered and regularly updated.
In this article, we’ll explore what a Cybersecurity Checklist is, why it’s essential, how you can implement it, and the best practices to follow. By the end, you’ll have a thorough understanding of how to maintain a secure digital environment for your business.
What is a Cybersecurity Checklist?
A Cybersecurity Checklist is essentially a structured document or tool designed to help organizations monitor and ensure that critical cybersecurity tasks are being completed regularly. It covers various elements such as system updates, data protection, backup strategies, and employee awareness. The ultimate goal of this checklist is to reduce vulnerabilities and create a more secure digital environment.
Typically, this checklist is broken down into specific tasks that need to be completed by designated individuals. It serves as a guide to make sure every part of your organization’s cybersecurity strategy is actively being managed and reviewed.
Key Features of a Cybersecurity Checklist Template
A well-designed Cybersecurity Checklist template offers several useful features. These elements are typically found in a template designed for quality control and easy tracking. Below are the key components of such a template:
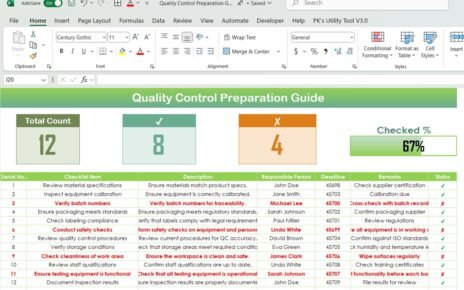
Cybersecurity Checklist Worksheet
Click to buy Cybersecurity
The checklist worksheet is the primary document where all tasks are captured. This worksheet allows you to list essential tasks and track their completion. The tasks are divided into individual items, each with a designated responsible person and deadline.
Status Tracking Section
To make it easier to monitor progress, the checklist template typically includes a status tracking section at the top. This section shows:
Total count of tasks
Checked count for completed tasks
Crossed count for tasks that are either completed or no longer applicable
Progress bar that visually represents the percentage of tasks that have been completed
This setup helps you easily visualize the progress made and identify areas that need more attention.
Detailed Checklist Table
The main part of the checklist is the table, where tasks are listed with detailed descriptions, assigned responsible persons, deadlines, and the current status. The tasks in the table are marked with either ✔ (completed) or ✘ (not completed).

Click to buy Cybersecurity
Advantages of Using a Cybersecurity Checklist
Using a Cybersecurity Checklist offers several significant benefits. Whether you are a small business or a large corporation, it helps you manage and improve your security efforts in a structured way. Below are some key advantages:
- Improved Security Posture: One of the biggest benefits of a cybersecurity checklist is that it helps organizations improve their overall security. By completing the listed tasks and regularly reviewing the checklist, companies can stay ahead of potential threats and reduce the risk of cyberattacks.
- Increased Efficiency: A checklist makes cybersecurity tasks easier to manage by providing clear instructions on what needs to be done. By assigning specific individuals to tasks and setting deadlines, everyone knows their responsibilities. This helps reduce confusion and ensures tasks are completed on time.
- Continuous Monitoring: Cyber threats are constantly evolving, which means that organizations need to stay vigilant. A checklist allows businesses to continuously monitor their systems and ensure that their cybersecurity measures are always up to date.
- Better Documentation: Cybersecurity audits and compliance checks require detailed documentation. With a checklist, organizations can maintain a clear record of completed tasks. This documentation can be helpful when reviewing cybersecurity policies or during audits.
- Enhanced Employee Awareness: Many cybersecurity incidents occur due to human error. A checklist ensures that employees are regularly trained and informed about potential risks. For example, a checklist may include tasks such as conducting phishing simulations or ensuring multi-factor authentication is enforced.
Opportunities for Improvement in Your Cybersecurity Checklist
While a cybersecurity checklist is a valuable tool, there’s always room for improvement. Here are some ways to enhance your checklist and make it more effective:
- Integrating Automation: Automation is a powerful way to streamline security processes. By using automated tools for vulnerability scanning, patch management, and system updates, you can reduce manual labor and improve efficiency. Automated updates can help ensure that critical tasks are not overlooked.
- Periodic Reviews: Cybersecurity threats and best practices evolve quickly. It’s essential to periodically review and update your checklist to reflect the latest risks and security standards. You should regularly assess the checklist to make sure it covers all areas of security, such as cloud security, data privacy, and threat intelligence.
- Expanding the Checklist’s Scope: As your organization grows, you may need to expand your checklist to include additional security measures. For example, you might add tasks related to employee access management, secure software development, or data encryption.
- Cross-Department Collaboration: Cybersecurity should not be confined to the IT department alone. Involve other teams, such as HR, legal, and finance, to ensure all aspects of security are covered. For instance, HR can help with employee training, while legal can assist with data privacy compliance.
Best Practices for Implementing a Cybersecurity Checklist
To get the most out of your cybersecurity checklist, consider implementing the following best practices:
- Assign Clear Responsibilities: It’s crucial to assign clear responsibilities for each task in the checklist. Ensure that everyone knows what they are accountable for and how to complete their tasks efficiently. This accountability will help ensure nothing is overlooked.
- Set Realistic Deadlines: While deadlines are important, they should also be realistic. Setting achievable deadlines will help ensure tasks are completed correctly and without unnecessary stress. Make sure deadlines are aligned with the complexity of the task.
- Regularly Monitor and Update the Checklist: A checklist is not something you can create once and forget about. It requires regular monitoring to ensure tasks are completed and to keep it up-to-date with the latest security developments. By continuously updating the checklist, you can adapt to new challenges and threats.
- Provide Employee Training: Employee awareness is key to preventing cyber threats. Regularly conduct training sessions to educate employees on the latest cybersecurity threats and how to recognize them, such as phishing emails and social engineering attacks. This training can be an integral part of your checklist.
- Use Analytics and Reporting Tools: To improve the effectiveness of your cybersecurity checklist, use analytics and reporting tools to track progress and identify areas for improvement. These tools can give you insights into which tasks are frequently delayed or overlooked, allowing you to make necessary adjustments.
Frequently Asked Questions (FAQs)
- Why Is a Cybersecurity Checklist Important?
A cybersecurity checklist is important because it helps ensure that all critical security measures are regularly completed and tracked. It serves as a guide for organizations to follow, reducing the likelihood of cyber threats and data breaches.
- How Often Should I Update My Cybersecurity Checklist?
It’s essential to review and update your cybersecurity checklist regularly. Ideally, you should do this at least once a quarter, but updates should also occur whenever new threats emerge or when changes are made to your IT infrastructure.
- Who Should Be Responsible for the Cybersecurity Checklist?
The responsibility for managing the cybersecurity checklist typically falls to the IT department or a designated cybersecurity team. However, departments such as HR and legal should also contribute, especially for tasks related to employee training and compliance.
- Can Automation Help With a Cybersecurity Checklist?
Yes, automation can improve the efficiency of a cybersecurity checklist. Tools that automatically scan for vulnerabilities, apply patches, and monitor security metrics can help reduce manual effort and ensure that tasks are completed consistently.
- How Do I Ensure Employees Follow the Cybersecurity Checklist?
To ensure compliance, assign clear responsibilities, provide regular training, and monitor progress. You should also conduct periodic audits to assess the effectiveness of the checklist and address any issues that arise.
Conclusion
In conclusion, a Cybersecurity Checklist is a vital tool for ensuring your organization remains secure in today’s fast-paced digital world. By following best practices and continuously improving your checklist, you can safeguard your systems, data, and employees from potential threats. The checklist not only helps you stay organized but also empowers you to take proactive steps in managing your organization’s cybersecurity.
Visit our YouTube channel to learn step-by-step video tutorials