Ensure your organization’s security protocols are flawlessly maintained with our Legal IT Security Policy Checklist Template in Excel. This comprehensive, ready-to-use template is tailored to assist IT departments in managing and tracking security measures effectively, ensuring compliance and safeguarding against potential threats.
Key Features of the IT Security Policy Checklist Template
Two Essential Worksheets:
IT Security Policy Checklist Tab:
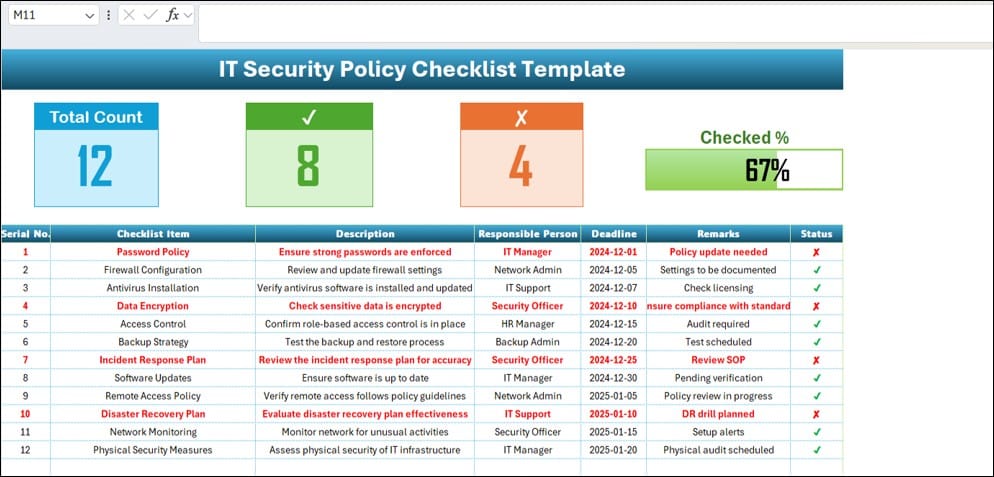
- The primary worksheet where you can document and track all critical IT security actions. It includes a dynamic progress bar and visual cards that display the total, checked, and crossed counts, providing a snapshot of your current security status.
List Sheet Tab:
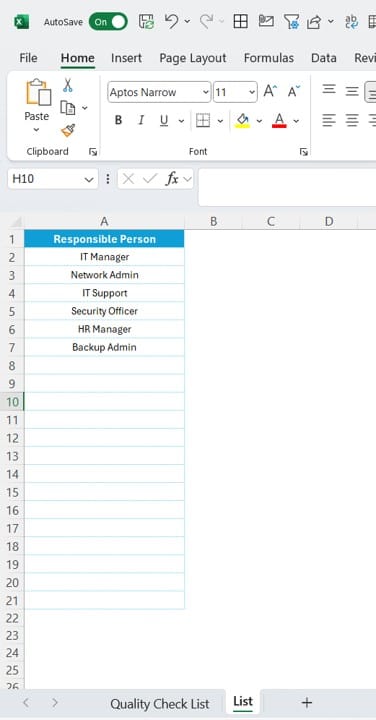
- Stores a unique list of responsible persons, allowing you to easily assign and manage tasks via a drop-down list in the main checklist table.
Detailed Checklist Table:
- Structured to capture comprehensive details including Serial No., Checklist Item, Description, Responsible Person, Deadline, Remarks, and Status. Update the status with a simple check (✔) or cross (✘) to reflect completion or pending tasks. This table facilitates a meticulous approach to maintaining robust IT security across various critical areas such as password policies, firewall configurations, antivirus installation, and more.
Read the detailed blog post