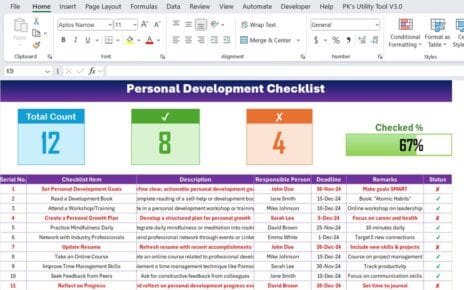
In today’s tech-driven landscape, safeguarding your IT infrastructure is crucial. Luckily, the IT Security Policy Checklist Template in Excel makes this task easier by providing a structured way to monitor and implement security measures. Let’s dive into how this template works and why it’s indispensable for IT teams.
Click to buy IT Security Policy
What is an IT Security Policy Checklist Template?
Essentially, this template helps you maintain a robust defines by ensuring every security task is accounted for—from enforcing strong passwords to updating firewalls and implementing encryption. The Excel format makes it super adaptable and easy to share, making it a practical tool for any IT team.
Key Features of the IT Security Policy Checklist Template
This well-designed template includes two main worksheets to help you manage IT security efficiently:
Click to buy IT Security Policy
IT Security Policy Checklist Tab
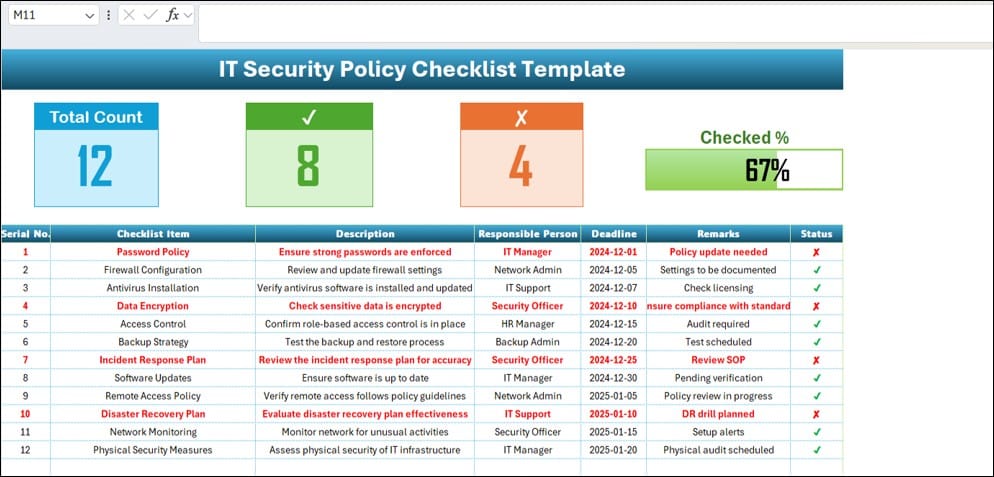
This is where you track your progress. Here’s what you’ll find:
Key Metrics at a Glance:
- Total Count: Displays all checklist items.
- Checked Count: Tracks completed items.
- Crossed Count: Shows what’s left to do.
- Progress Bar: Visually indicates how much of the work is done.
Detailed Checklist Table:
- Serial No.: Unique identifier for each task.
- Checklist Item: Task title.
- Description: What the task involves.
- Responsible Person: Who is in charge.
- Deadline: When it needs to be done by.
- Remarks: Additional notes.
- Status: Done or pending.
List Sheet Tab
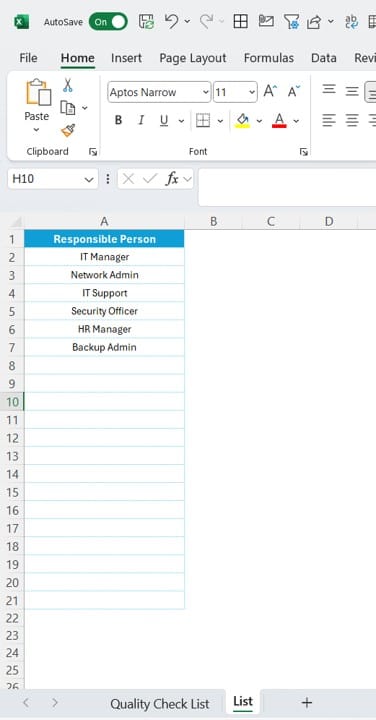
- This supplementary sheet stores team member names for task assignments, enhancing user-friendliness and ensuring consistency.
Click to buy IT Security Policy
Why Should You Use This Template?
- Organizes Your Tasks: Everything security-related in one place.
- Enhances Accountability: Clear assignments mean no overlaps or confusion.
- Saves Time: The layout and indicators make tracking straightforward.
- Ensures Compliance: Helps meet industry standards and legal requirements.
- Getting Started: How to Use the IT Security Policy Checklist Template
- List the Tasks: Start by noting down all necessary security tasks.
- Assign Responsibly: Delegate tasks using the built-in drop-down menus.
- Set Realistic Deadlines: Ensure each task has a clear deadline.
- Track Your Progress: Mark tasks as completed or pending.
- Review Regularly: Keep tabs on your progress with the summary cards and progress bar.
Best Practices for Optimal Use
- Customize as Needed: Tailor tasks and timelines to fit your specific security needs.
- Collaborate Widely: Involve various departments to cover all bases.
- Keep it Updated: Adjust the checklist as your organization evolves.
- Conduct Regular Audits: Verify that completed tasks meet your standards.
Click to buy IT Security Policy
Advantages of This Template
- User-Friendly: Easy for anyone to use, regardless of their tech skill level.
- Comprehensive: Provides a full view of your security status at a glance.
- Efficient: Reduces the time spent on manual security management.
Opportunities for Improvement
- Train Your Team: Make sure everyone understands their role in IT security.
- Automate Where Possible: Use tools to automate routine tasks.
- Gather Feedback: Regularly refine the checklist based on team input.
Frequently Asked Questions
- Why is this checklist crucial? It helps ensure no critical security task is missed, keeping your organization safe and compliant.
- Can I customize the template? Absolutely! It’s designed to be modified to suit your specific needs.
- How often should I review the checklist? At least quarterly, or more often if there are significant changes in your IT environment.
- Is the progress bar automated? Yes, it updates itself based on task completion.
- What are some must-have tasks for the checklist? Include password policies, firewall configurations, encryption standards, and incident response strategies.
Click to buy IT Security Policy
Conclusion
The IT Security Policy Checklist Template in Excel is a vital tool for any organization aiming to protect its IT infrastructure. It simplifies security management, keeps your team aligned, and ensures you stay on top of all necessary precautions. Start using this template today to foster a safer, more secure operational environment.
Visit our YouTube channel to learn step-by-step video tutorials
View this post on Instagram
Click to buy IT Security Policy